Error: ‘Security package error occurred in the transport layer’ when connecting to the Hosted platform
Error: Security package error occurred in the transport layer for Windows 10 users trying to connect to Scomis Hosted Applications platform.
This issue is affecting Windows 10 users that are connecting to the legacy gateway server for Windows 7 machines. The following FAQ http://faq.scomis.org/kb11624/ has more information related to the specific gateway servers. The default gateway server is gw-eclipse.rdp.scomis.org with requires access to 109.176.106.251 on TCP port 443, the backup is gw-swgfl.rdp.scomis.org (217.179.30.29) on TCP port 443. If you are doing SSL inspection/interception you need to add the same addresses into your exclusion list so they are not intercepted. GW.scomis.org is the legacy server, which seems to be allowing connection attempts but due to a Windows 10 security setting, it gives those clients the error message you are receiving.
We have been trying to investigate this issue with Microsoft’s assistance however at the moment we don’t have a permanent fix.
There are a couple of potential workarounds to this issue. is to replace the mstsc.exe and mstscax.dll files located in C:\Windows\SysWOW64\ and C:\Windows\System32\ on the workstations unable to connect with the same files from a Windows 10 workstation that is able to connect to SIMS without this issue.
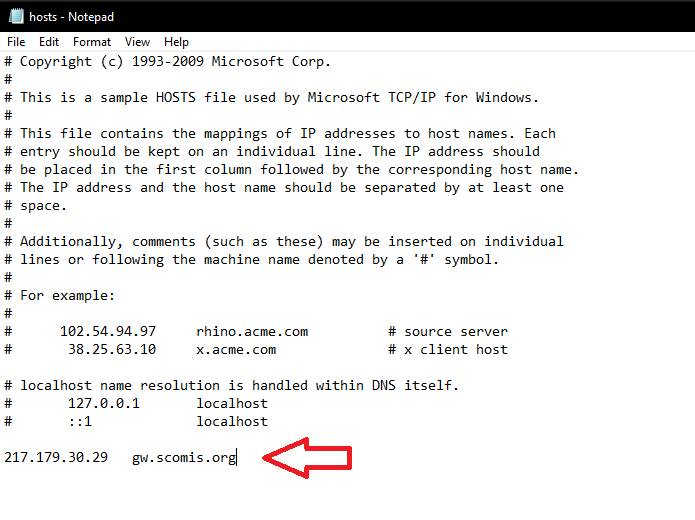
Alternatively you can force connections to use the updated gateway servers by amending your Hosts file, adding in the following line:
217.179.30.29 gw.scomis.org
The hosts file can be located in the C:\Windows\System32\drivers\etc\ directory on each workstation.
Further guidance on editing your hosts file can be found at the following link. https://www.howtogeek.com/howto/27350/beginner-geek-how-to-edit-your-hosts-file/
This document will be updated as further information becomes available.
Background information:
The Remote Desktop Client which is part of Windows 10 uses a new method of connecting to a remote computer when the connection is configured to use a Remote Desktop Gateway connection. This method is simply called “HTTP”. The HTTP method promises to be more efficient and secure than the previous “RPC over HTTP” method that was used in Server 2008 and Server 2012.
The Remote Desktop client negotiates a connection method to send the Remote Desktop Protocol (RDP) data to the Gateway Server. When connecting to a Server 2008 Gateway, the method will be negotiated to use RPC over HTTP. If a Server 2016 Gateway is providing the bridge, the new HTTP method will be used. The client will then fall back to the RPC over HTTP method if the negotiation fails.
Unfortunately it appears that the developers of the protocol have not documented how and when the client will fail over to the back up protocol. It is also possible that the protocol is not proxy/IDS friendly which also results in a problem.